Malware analysis report: SNOWYAMBER (+APT29 related malwares)
This report provides a comprehensive analysis of the SNOWYAMBER dropper, and it’s modifications, a sophisticated piece of malware attributed to the Advanced Persistent Threat group APT29. The group is believed to be tied to the Russian government and has been linked to numerous cyber espionage operations.
Threat actor
APT29, also known as The Dukes or Cozy Bear, is a highly sophisticated and well-resourced cyber espionage group believed to be associated with the Russian government. It has been operating since at least 2008.
Target
While the group’s exact location is unknown, multiple cybersecurity research groups and government agencies attribute APT29 to Russia. Their targets are typically spread across the globe, with a specific focus on government organizations, think-tanks, healthcare organizations, and energy sectors.
TTPs
APT29 is known for its persistent and evolving tactics, which include a combination of advanced techniques and procedures:
Spear-Phishing: APT29 commonly utilizes spear-phishing campaigns for initial compromise. These usually involve emails with either a malicious attachment or a link to a malicious website. Their spear-phishing attacks often involve the use of legitimate web services, such as Google accounts, to host their payload and seem less suspicious.
Use of Zero-days and Exploits: The group is known to use zero-day exploits as well as known vulnerabilities to infiltrate networks. They were known to exploit vulnerabilities such as CVE-2017-11292 (Adobe Flash), CVE-2017-8759 (.NET Framework), and CVE-2017-0199 (Microsoft Office/WordPad).
Living-off-the-Land Tactics: APT29 frequently employs “living-off-the-land” tactics, where they use legitimate system tools and processes to hide their activities and maintain persistence. For instance, they have been known to use PowerShell for scripting, WMI for persistence, and PsExec for lateral movement.
Custom Malware: The group uses a variety of custom backdoors and droppers, including but not limited to MiniDuke, CosmicDuke, OnionDuke, and CozyDuke. More recently, they have been associated with the WellMess and WellMail malware.
Stealth and Long-term Persistence: APT29 is known for its stealthy operations and ability to maintain a long-term presence on infiltrated networks without detection. They often do so by limiting their activities during the working hours of the target’s local time zone to mimic legitimate users and avoid raising alerts.
Data Exfiltration: APT29 is known for extracting sensitive information from the infiltrated networks. They often do this very slowly and cautiously to avoid detection. The group is believed to be interested in gathering intelligence related to foreign policy, defense, international relations, and similar topics.
Malware features
Through our analysis, we have identified the following notable features of the SNOWYAMBER dropper:
Infection capabilities: The malware is typically introduced to the victim’s machine via spear phishing, hiding in documents that prompt the user to enable macros. (High Confidence)
Capacity for self-preservation: The malware employs anti-analysis and persistence mechanisms, which include obfuscation techniques, disabling security tools, and creating Registry keys to survive reboots. (High Confidence)
Diffusion mechanism: The dropper, upon execution, deploys additional payloads on the infected machine, and may also propagate laterally within the network. (Medium Confidence)
Data exfiltration capabilities: The malware appears capable of collecting system information and sending it to a Command and Control (C2) server. (High Confidence)
C2 mechanisms: The malware uses encrypted HTTP requests for C2 communication. (High Confidence)
Identification
Among the malware samples analysed, the most interesting are following.
Three samples are being investigated:
sample.exe – this file is worked for injection:
File size: 205824 bytes
MD5 sum: 109f05770bf8550f71b39ceaffc6e42e
SHA-1 sum: 72b57b47649f145ba341420fa0a4624810c011d9
SHA-256 sum: 287543c235cf68695373d367144c51a0236879e614e8ea4634b82e5336785edc
First of all, check our sample via VirusTotal:
So, 2 of 70 AV engines detect our sample as malicious.
This sample is written in C++ and uses multiple malware development tricks: WinAPI functions call by hash, string obfuscation and encryption, time distortion.
Static analysis
The specified sample is a PE file:
Use exiftool for looking metadata:
And we see that file timestamp is 2023-02-25 22:07:22+03.00
Executable sample is not packed by upx:
What about Shannon entropy of the sample:
Analysze with DIE says that the compiler is Microsoft Visual Studio 2019:
dynamic analysis
Contacted IP addresses is:
The main logic starts with the int start function.
Then arbitrary computations are performed: this is a popular sandbox bypass trick. And run switch logic:
Also use WinAPI functions:
CreateTimerQueue
CreateTimerQueueTimer
DeleteTimerQueueEx
Here use an event object to track the TimeRoutine execution, create the timer queue, then set a timer to call the timer routine in 10 seconds.
This implementation sets up asynchronous timers using CreateTimerQueueTimer. Each executes one after the other and does the following tasks: Wait a specific time period.
When executed, the injector reads the resource, decrypts it by RC4 algorithm, allocates memory, copies sections, processes relocks, and transfers control to the entry point.
What about injection technique. It’s PE injection.
All NT API functions are replaced by calling equivalent syscalls from https://github.com/klezVirus/SysWhispers3.
sample2.exe – this sample is an encryptor:
File size: 214528 bytes
MD5 sum: 107dae5b9c61c962e0d604cd70a1d8ae
SHA-1 sum: 3752be6b162bacb0d7c12b6d122c9dbaf3ad6223
SHA-256 sum: a89150f159c1c9d053365ac38625f783642bc4c16a693cb106d715819acc677b
Check it via VirusTotal:
So, 2 of 70 AV engines detect our sample as malicious.
This encryptor encrypts the payload with the RC4 algorithm, then the result is attached to the injector with the resource.
Encryptor use 2 params: Input file and output file.
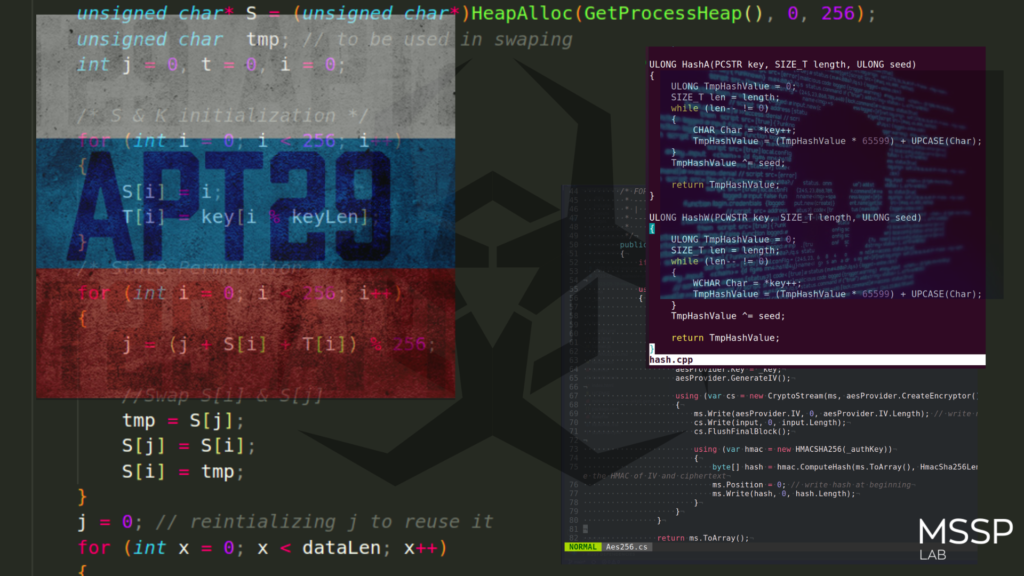
Classic RC4 algorithm:
There is a simple reimplementation this logic:
unsigned char* T = (unsigned char*)HeapAlloc(GetProcessHeap(), 0, 256);
unsigned char* S = (unsigned char*)HeapAlloc(GetProcessHeap(), 0, 256);
unsigned char tmp; // to be used in swaping
int j = 0, t = 0, i = 0;
/* S & K initialization */
for (int i = 0; i < 256; i++) {
S[i] = i;
T[i] = key[i % keyLen];
}
/* State Permutation */
for (int i = 0; i < 256; i++) {
j = (j + S[i] + T[i]) % 256;
//Swap S[i] & S[j]
tmp = S[j];
S[j] = S[i];
S[i] = tmp;
}
j = 0; // reintializing j to reuse it
for (int x = 0; x < dataLen; x++) {
i = (i + 1) % 256; // using %256 to avoid exceed the array limit
j = (j + S[i]) % 256; // using %256 to avoid exceed the array limit
//Swap S[i] & S[j]
tmp = S[j];
S[j] = S[i];
S[i] = tmp;
t = (S[i] + S[j]) % 256;
data[x] = data[x] ^ S[t]; // XOR generated S[t] with Byte from the plaintext / cipher and append each Encrypted/Decrypted byte to result array
}
HeapFree(GetProcessHeap(), 0, T);
HeapFree(GetProcessHeap(), 0, S);
}
The encryption/decryption key is:
sample3.exe – this sample plays the role of a reverse shell:
File size: 9216 bytes
MD5 sum: 68d957f5fbb2f2078da9059995ece969
SHA-1 sum: 545ccdb7e68c6cef6271698c0815db33625aae03
SHA-256 sum: 6dc1393ccacd031fa0141aa312d55deb2552a7a95c3ae21856c82beb21a554bd
First of all, check our sample via VirusTotal:
So, 14 of 71 AV engines detect our sample as malicious.
More of them detect file as Gen:Heur.Loregun.19.
Contacted IP addresses:
The logic of this sample is pretty simple: create a socket, listen on it, transfer all I/O to the socket.
Malware evasion tricks
RVA to offset:
We restored WinAPI hashing logic:
(((wch) >= ‘a’) && ((wch) <= ‘z’) ?
(wch)
:
((wch) + (‘a’-‘A’))
)
ULONG HashA(PCSTR key, SIZE_T length, ULONG seed) {
ULONG TmpHashValue = 0;
SIZE_T len = length;
while (len– != 0) {
CHAR Char = *key++;
TmpHashValue = (TmpHashValue * 65599) + UPCASE(Char);
}
TmpHashValue ^= seed;
return TmpHashValue;
}
ULONG HashW(PCWSTR key, SIZE_T length, ULONG seed) {
ULONG TmpHashValue = 0;
SIZE_T len = length;
while (len– != 0) {
WCHAR Char = *key++;
TmpHashValue = (TmpHashValue * 65599) + UPCASE(Char);
}
TmpHashValue ^= seed;
return TmpHashValue;
}
and hashing table:
0xc4f4eb06,//AmsiOpenSession
0xea48872c,//CloseHandle
0x3bc77547,//closesocket
0x96d3ba46,//connect
0x8278b698,//CreateMutexW
0x609502e8,//CreateProcessW
0x1347fdfd,//ExitProcess
0x27bcb342,//ExpandEnvironmentStringsW
0x5366ed60,//FreeAddrInfoW
0x39c8604e,//GetAddrInfoW
0x26f75d64,//GetCurrentThreadId
0x55e2cac2,//GetFileAttributesW
0xab26d610,//GetLastError
0xbd71d0e0,//LoadLibraryA
0xbd71d0ce,//LoadLibraryW
0x23dcad1c,//lstrcatA
0xd84484d6,//lstrcpyA
0x23dcad6a,//lstrcatW
0xdfc07835,//lstrcmpiA
0xdfc07803,//lstrcmpiW
0xd844bb3c,//lstrcpyW
0x468d52ab,//lstrlenW
0x468d525d,//lstrlenA
0xf94e8b9f,//MessageBoxW
0x326d0bc9,//MultiByteToWideChar
0x11983657,//NtTraceEvent
0x9293ab58,//OutputDebugStringW
0xc83db0b4,//ReleaseMutex
0xbdcac89f,//RtlAllocateHeap
0x3c3e5b30,//RtlCompareMemory
0x1dc948b0,//RtlMoveMemory
0x3519f2b9,//RtlDosPathNameToNtPathName_U
0xce521091,//RtlExitUserThread
0x4ead0e2e,//RtlFreeHeap
0xfc4d07c0,//RtlGetVersion
0xe24742d8,//RtlInitUnicodeString
0xb1d4a311,//RtlNtStatusToDosError
0x819c55ff,//RtlZeroMemory
0xd66bb51c,//SetLastError
0x0f8a6e1b,//Sleep
0x036a4566,//VirtualAlloc
0x0033e9b1,//VirtualAllocEx
0xc7433c7b,//VirtualFree
0xaa9a1e06,//VirtualFreeEx
0x61462271,//VirtualQuery
0x9f79559c,//WaitForMultipleObjects
0x4b570e37,//WaitForSingleObject
0x85729171,//WideCharToMultiByte
0x874700d3,//WSACleanup
0x90b71e53,//WSASocketW
0xa48ed094,//WSAStartup
0xfdb3b358,//wvsprintfA
0xfdb3b3a6//wvsprintfW
IOCs
Sigma rule
id: a1a144b7-5c9b-4853-a559-2172be8d4a03
related:
– id: f016c716-754a-467f-a39e-63c06f773987
type: obsoletes
status: experimental
description: Detects uncommon target processes for remote thread creation
references:
– https://blog.redbluepurple.io/offensive-research/bypassing-injection-detection
author: Florian Roth (Nextron Systems)
date: 2022/03/16
modified: 2023/05/05
tags:
– attack.defense_evasion
– attack.privilege_escalation
– attack.t1055.003
logsource:
product: windows
category: create_remote_thread
detection:
selection:
TargetImage|endswith:
– ‘calc.exe’
– ‘calculator.exe’
– ‘explorer.exe’
– ‘mspaint.exe’
– ‘notepad.exe’
– ‘ping.exe’
– ‘sethc.exe’
– ‘spoolsv.exe’
– ‘wordpad.exe’
– ‘write.exe’
filter_optional_aurora_1:
StartFunction: ‘EtwpNotificationThread’
filter_optional_aurora_2:
SourceImage|contains: ‘unknown process’
filter_main_spoolsv:
SourceImage: ‘C:WindowsSystem32csrss.exe’
TargetImage: ‘C:WindowsSystem32spoolsv.exe’
condition: selection and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
– Unknown
level: high
Conclusion
Running code in the context of another process may allow a threat actor to access the process’s memory, system/network resources, and possibly elevated privileges. PE injection is commonly used by malware for persistent infection and evasion of detection.
LoadPE Injection is a technique that involves loading a PE file into the memory of a process. In a typical LoadPE Injection scenario, the following steps occur:
The malware allocates space in its own process for the PE file.
The malware reads the PE file from disk into the allocated space.
The malware resolves import addresses for the PE file.
The malware creates a remote thread in a target process.
The malware injects the PE file into the address space of the target process.
The malware initiates execution of the injected PE file in the target process.
This technique allows malware to avoid many behavioral detection strategies. It allows the malicious PE to be executed without ever being directly loaded or written to the disk, making it more difficult for traditional antivirus software to detect.
As we can see, the technique is not new but is still used in 2023.
We believe that this is either a new modification of Snowyamber or a new Conti style malware family, since any Russian related groups use ContiLeaks. ContiLeaks is a turning point in the cybercrime ecosystem, and in this case, we can expect a lot of changes in how cybercriminal organizations operate.
By Cyber Threat Hunters from MSSPLab:
References
APT29
SNOWYAMBER Malware Analysis Report
https://github.com/SigmaHQ/sigma
Process Injection
Thanks for your time happy hacking and good bye!
All drawings and screenshots are MSSPLab’s
Article Link: Malware analysis report: SNOWYAMBER (+APT29 related malwares) – MSSP Lab
1 post – 1 participant
